Security at Legito
Data security and privacy are the highest priority for Legito
Highest priority
ISO 27001 certification
We have been approved by Lloyd’s Register to the rigorous international standards for security and quality found in ISO/IEC 27001:2013 for:
“Developing and hosting Legito document automation and contract lifecycle management software. Providing document automation and software configuration services.”
For Legito, ISO:IEC 27001:2013 certification means that we are using recognized international requirements for the security and quality of our internal processes that includes designing, developing, hosting and supporting the most precious thing we have – our Legito application where your customers store their data.
The latest ISO 27001 audit was conducted in July 2021.


Our team has relevant experience
Hosted in world class facilities
The vast majority of our services and data are hosted in OVH facilities in the USA, EU, and Australia. OVH data centres have the very highest security standards and hold the following certifications:
- ISO/IEC 27001 certification
- SOC 1 Type II and SOC 2 Type II certification.
- PCI DSS Certification.
- STAR self-assessment – Cloud Security Alliance.
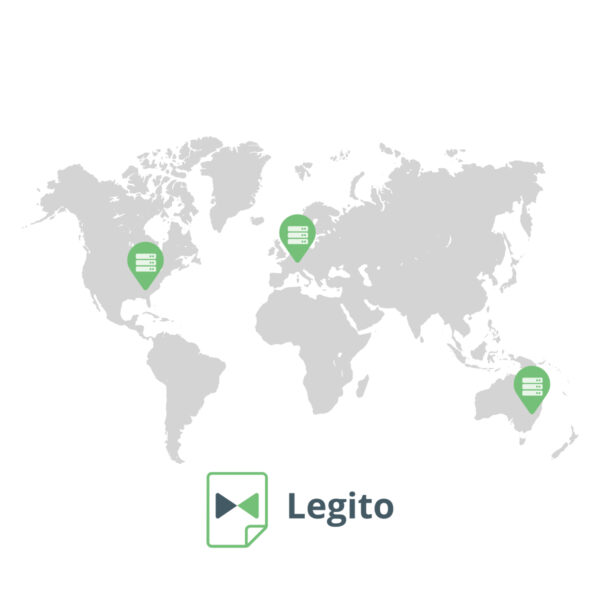
Global server infrastructure
Each customer may choose their data storage location. Legito currently has the following available hosting locations:
- Vint Hill, Virginia, USA
- Limburg, Germany, EU
- Melbourne, Victoria, Australia
We encrypt your data
We follow best practices
At Legito we follow best practices that improve our security posture, including:
- We have functioning, frequently-used automation in place so that we can safely and reliably roll out changes to our application within minutes. We have high confidence that we can get a security fix out quickly if necessary.
- We use market standard technologies to provide an audit trail over our infrastructure and the Legito application. Auditing allows us to do ad-hoc security analysis, track changes made to our setup and audit access to every layer of our stack.
- We use two-factor authentication whenever appropriate.
- We have a documented incident response plan and educate all staff on security procedures and policies including evaluation and continuous improvement.
- We have strong password policies.
- We have manual as well as automated testing in place, including unit tests.
- We perform at least two code reviews of each new feature and patch.
We enable security features
We have lots of features that allow our customers to use Legito with enhanced security. These include:
- Robust access control list.
- IP address login restrictions.
- Customizable password requirements for each Workspace.
- Users’ inactivity logouts.
- Use of the Legito shutdown method to end a session.
- Timeline (audit trail) and versioning.
- Self generating, deactivating and deleting API keys.
- Self anonymization of data in Legito documents.
Regular customer audits
We do not store payment details