Single Sign-On
Learn about SSO
Single sign-on (SSO) is an authentication scheme that allows a user to log in once with a single ID to multiple
independent software systems.
Legito supports SSO according to your chosen plan (see https://www.legito.com/pricing/)
The following SSO providers are currently supported by Legito:
Azure AD
Documentation: https://learn.microsoft.com/entra/identity/enterprise-apps/one-click-sso-tutorial
Configuration: https://www.legito.com/developers/oauth-2-0-authentication-with-azure-active-directory/
Okta
Documentation: https://www.okta.com/customer-identity/single-sign-on/
Configuration:https://help.okta.com/en-us/content/topics/apps/apps_app_integration_wizard_oidc.htm
JumpCloud
Documentation: https://jumpcloud.com/platform/single-sign-on
Configuration: https://jumpcloud.com/support/sso-with-oidc
If you use another SSO provider, please let us know via automation@legito.com.
How to set up SSO
- Contact Legito support via automation@legito.com with your SSO request.
- We will create a 3rd level domain (<yourcompanyname>.legito.com)
- We will enable the SSO feature in your Settings.
- Legito will assign you with a specific subdomain yourcompanyname.legito.com. You need to use your assigned
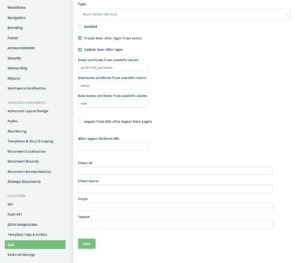
subdomain for SSO. - Go to Settings > SSO and complete the input fields as illustrated below:
Legend for fields
Type
set your SSO provider
Create User after login if it does not exist
When set correctly, Legito will automatically create a new user with a role marked as Default (See Tab Roles &
Permissions). If not set correctly, and a user is not pre-created in ‘People’, the user will be denied access.
Update User after login
When set, user details (username/roles/permissions) will be updated and local changes will be discarded. If not set,
changes made in Legito will remain.
Email attribute from userinfo claims
Fill in the name of the attribute (in the SSO message) where the email identity will be filled in. Typically email,
or useremail.
The email address as a primary key for identifying users. If their email address is changed, their user identity
changes too.
Username attribute from userinfo claims
Fill in a name of the attribute (in the SSO message) where the user name can be found. Typically
preferred_username or username.
Role Name attribute from userinfo claims
Fill in a name of an attribute (in the SSO message) where the role can be found. This attribute value has to match
the Identifier from the “Roles & Permissions” tab.
Logout from SSO after logout from Legito
This Option redirects users to the logout page of the SSO provider, so the user will also be logged out of the
SSO.
After Logout redirect URI
When filled, Legito will redirect the user to the defined URI. Otherwise, the user is redirected to the login page
(which will redirect the user to your SSO provider).
Client ID and Client Secret
Provided by your SSO provider.
Scope
Complete all the claims you want to use in the fields above: typically: preferred_name, email, username, role. SSO can send those anyway and ignore the requested scope.
Tenant
Complete in case of Azure AD SSO. (see details here
https://www.legito.com/developers/oauth-2-0-authentication-with-azure-active-directory/)